
Based on the ever-encroaching surveillance systems used by local and national governments and private organizations one has to wonder if we — the presumed innocent — are living inside or outside a prison facility. Advances in security and surveillance systems now make it possible to track swathes of the population over periods of time across an entire city.
From the Washington Post:
Shooter and victim were just a pair of pixels, dark specks on a gray streetscape. Hair color, bullet wounds, even the weapon were not visible in the series of pictures taken from an airplane flying two miles above.
But what the images revealed — to a degree impossible just a few years ago — was location, mapped over time. Second by second, they showed a gang assembling, blocking off access points, sending the shooter to meet his target and taking flight after the body hit the pavement. When the report reached police, it included a picture of the blue stucco building into which the killer ultimately retreated, at last beyond the view of the powerful camera overhead.
“I’ve witnessed 34 of these,” said Ross McNutt, the genial president of Persistent Surveillance Systems, which collected the images of the killing in Ciudad Juarez, Mexico, from a specially outfitted Cessna. “It’s like opening up a murder mystery in the middle, and you need to figure out what happened before and after.”
As Americans have grown increasingly comfortable with traditional surveillance cameras, a new, far more powerful generation is being quietly deployed that can track every vehicle and person across an area the size of a small city, for several hours at a time. Though these cameras can’t read license plates or see faces, they provide such a wealth of data that police, businesses, even private individuals can use them to help identify people and track their movements.
Already, the cameras have been flown above major public events, such as the Ohio political rally where Sen. John McCain (R-Ariz.) named Sarah Palin as his running mate in 2008, McNutt said. They’ve been flown above Baltimore; Philadelphia; Compton, Calif.; and Dayton in demonstrations for police. They’ve also been used for traffic impact studies, for security at NASCAR races — and at the request of a Mexican politician, who commissioned the flights over Ciudad Juarez.
Video: A time machine for police, letting them watch criminals—and everyone else.
Defense contractors are developing similar technology for the military, but its potential for civilian use is raising novel civil-liberty concerns. In Dayton, where Persistent Surveillance Systems is based, city officials balked last year when police considered paying for 200 hours of flights, in part because of privacy complaints.
“There are an infinite number of surveillance technologies that would help solve crimes .?.?. but there are reasons that we don’t do those things, or shouldn’t be doing those things,” said Joel Pruce, a University of Dayton post-doctoral fellow in human rights who opposed the plan. “You know where there’s a lot less crime? There’s a lot less crime in China.”
McNutt, a retired Air Force officer who once helped design a similar system for the skies above Fallujah, a key battleground city in Iraq, hopes to win over officials in Dayton and elsewhere by convincing them that cameras mounted on fixed-wing aircraft can provide far more useful intelligence than police helicopters do, for less money. The Supreme Court generally has given wide latitude to police using aerial surveillance so long as the photography captures images visible to the naked eye.
A single camera mounted atop the Washington Monument, McNutt boasts, could deter crime all around the National Mall. He thinks regular flights over the most dangerous parts of Washington — combined with publicity about how much police could now see — would make a significant dent in the number of burglaries, robberies and murders. His 192-megapixel cameras would spot as many as 50 crimes per six-hour flight, he estimates, providing police with a continuous stream of images covering more than a third of the city.
“We watch 25 square miles, so you see lots of crimes,” he said. “And by the way, after people commit crimes, they drive like idiots.”
What McNutt is trying to sell is not merely the latest techno-wizardry for police. He envisions such steep drops in crime that they will bring substantial side effects, including rising property values, better schools, increased development and, eventually, lower incarceration rates as the reality of long-term overhead surveillance deters those tempted to commit crimes.
Dayton Police Chief Richard Biehl, a supporter of McNutt’s efforts, has even proposed inviting the public to visit the operations center, to get a glimpse of the technology in action.
“I want them to be worried that we’re watching,” Biehl said. “I want them to be worried that they never know when we’re overhead.”
Technology in action
McNutt, a suburban father of four with a doctorate from the Massachusetts Institute of Technology, is not deaf to concerns about his company’s ambitions. Unlike many of the giant defense contractors that are eagerly repurposing wartime surveillance technology for domestic use, he sought advice from the American Civil Liberties Union in writing a privacy policy.
It has rules on how long data can be kept, when images can be accessed and by whom. Police are supposed to begin looking at the pictures only after a crime has been reported. Pure fishing expeditions are prohibited.
The technology has inherent limitations as well. From the airborne cameras, each person appears as a single pixel indistinguishable from any other person. What they are doing — even whether they are clothed or not — is impossible to see. As camera technology improves, McNutt said he intends to increase their range, not the precision of the imagery, so that larger areas can be monitored.
The notion that McNutt and his roughly 40 employees are peeping Toms clearly rankles. They made a PowerPoint presentation for the ACLU that includes pictures taken to aid the response to Hurricane Sandy and the severe Iowa floods last summer. The section is titled: “Good People Doing Good Things.”
“We get a little frustrated when people get so worried about us seeing them in their back yard,” McNutt said in his operation center, where the walls are adorned with 120-inch monitors, each showing a different grainy urban scene collected from above. “We can’t even see what they are doing in their backyard. And, by the way, we don’t care.”
Yet in a world of increasingly pervasive surveillance, location and identity are becoming all but inextricable — one quickly leads to the other for those with the right tools.
During one of the company’s demonstration flights over Dayton in 2012, police got reports of an attempted robbery at a bookstore and shots fired at a Subway sandwich shop. The cameras revealed a single car moving between the two locations.
By reviewing the images, frame by frame, analysts were able to help police piece together a larger story: The man had left a residential neighborhood midday, attempted to rob the bookstore but fled when somebody hit an alarm. Then he drove to Subway, where the owner pulled a gun and chased him off. His next stop was a Family Dollar Store, where the man paused for several minutes. He soon returned home, after a short stop at a gas station where a video camera captured an image of his face.
A few hours later, after the surveillance flight ended, the Family Dollar Store was robbed. Police used the detailed map of the man’s movements, along with other evidence from the crime scenes, to arrest him for all three crimes.
On another occasion, Dayton police got a report of a burglary in progress. The aerial cameras spotted a white truck driving away from the scene. Police stopped the driver before he got home from the heist, with the stolen goods sitting in the back of the truck. A witnessed identified him soon after.
Read the entire story here.
Image: Surveillance cameras. Courtesy of Mashable / Microsoft.






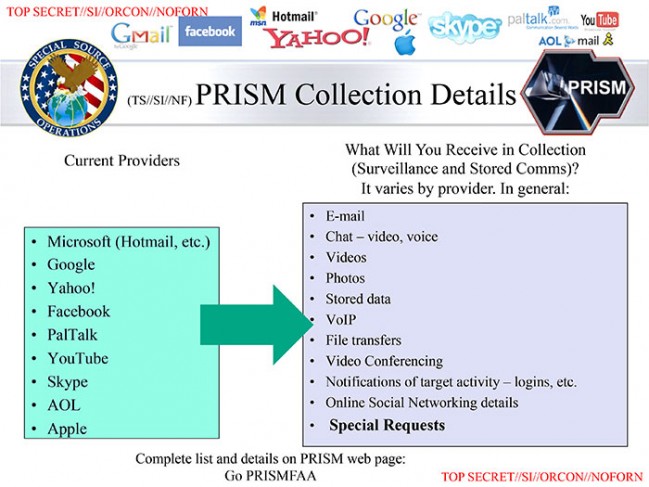
 Ubiquitous connectivity for, and between, individuals and businesses is widely held to be beneficial for all concerned. We can connect rapidly and reliably with family, friends and colleagues from almost anywhere to anywhere via a wide array of internet enabled devices. Yet, as these devices become more powerful and interconnected, and enabled with location-based awareness, such as GPS (Global Positioning System) services, we are likely to face an increasing acute dilemma — connectedness or privacy?
Ubiquitous connectivity for, and between, individuals and businesses is widely held to be beneficial for all concerned. We can connect rapidly and reliably with family, friends and colleagues from almost anywhere to anywhere via a wide array of internet enabled devices. Yet, as these devices become more powerful and interconnected, and enabled with location-based awareness, such as GPS (Global Positioning System) services, we are likely to face an increasing acute dilemma — connectedness or privacy?